The Device Identifier Composition Engine (DICE) is a Trusted Computing Group (TCG) specification that has been adopted into Android. It creates a set of strong, immutable cryptographic identities for each piece of firmware loaded during the boot sequence. These identities enable remote verification of a device's security posture, which can only be evaded by compromising the ROM.
DICE derivation process
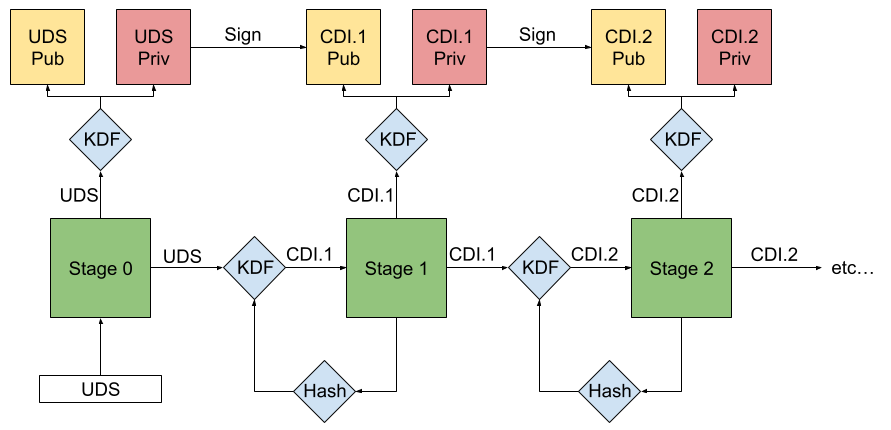
Figure 1. Simplified DICE derivation process.
The DICE derivation process ensures that any change to any firmware image results in a new unique identifier for that stage and every stage thereafter. This is because each loaded firmware stage measures and certifies the next, generating unique identities and associated keys that prevent bypassing or tampering. The read-only memory (ROM) processes the measurement, configuration, and unique device secret (UDS) with a key derivation function (KDF) to derive the secret for the next stage to be loaded. This secret is referred to as a compound device identifier (CDI).
Stage 0: Initialization
The DICE process begins with the chipset’s ROM loading the UDS from a bank of immutable data, typically fuses. This UDS is securely provisioned with a cryptographically random value during the chip production process. After reading the UDS, the ROM uses a vendor-dependent hardware-locking mechanism such as a latch to lock UDS access until the next boot.
Stage 1: Initial key derivation
The ROM uses the UDS as input to a key derivation function (KDF) to generate the permanent asymmetric key pair that uniquely identifies that device. It measures the next firmware stage, including metadata about the boot environment such as whether secure boot is enabled. The ROM then combines the UDS, firmware measurement, and configuration data in the KDF to derive the first CDI, which is passed to the next stage as a secret.
Stage 2 to n: Recursive key derivation
The process then repeats. In all subsequent stages, the CDI from the previous stage serves as the input for a new KDF. This KDF uses the CDI and the hash of the next firmware image to produce a new derived CDI. Each stage generates its own key pair and uses it to sign a certificate containing stage-specific measurements and other associated metadata.
